Cybersecurity Crisis Response Plan (1/2)
In the NIST framework, cybersecurity is divided into 5 pillars : identify, detect protect, respond and recover. When discussing a cybersecurity crisis we are effectively dealing with the last two pillars trying both to respond to an attack and also trying to recover as fast as possible.

Definition and prerequisites
A vulnerability is a weakness in security systems that can be attacked allowing an attacker to perform unauthorized actions (e.g., SQL injection) or permits undesirable situations to occur (e.g., absence of backups).
A cyber-attack always begins with the exploitation of a vulnerability (automated or manual). This is the first step in a chain of events. In normal circumstances, the exploitation of a vulnerability should be detected by the SOC.
When the exploitation of a vulnerability is achieved (an exploit), the event(s) can be qualified as a cybersecurity incident. A cybersecurity incident is an anomaly that could potentially or has effectively affected activities of a business unit (operational, strategic, reputation...).
Under some circumstances, an incident can be reclassified as a crisis. The criteria allowing for a re-qualification are defined in the crisis management plan rather than the crisis response plan. A crisis can be of many forms, a pandemic is also a crisis in that regard. Each company will need to define what a crisis actually is depending on the kind of incident (cyber, HR, political, environmental...).
Generally speaking, a cybersecurity incident becomes a crisis when either (or both):
- The usual processes to manage the incident cannot function properly.
- The potential impact are so great we want to engage in an effort to diminish the impact as soon as possible.
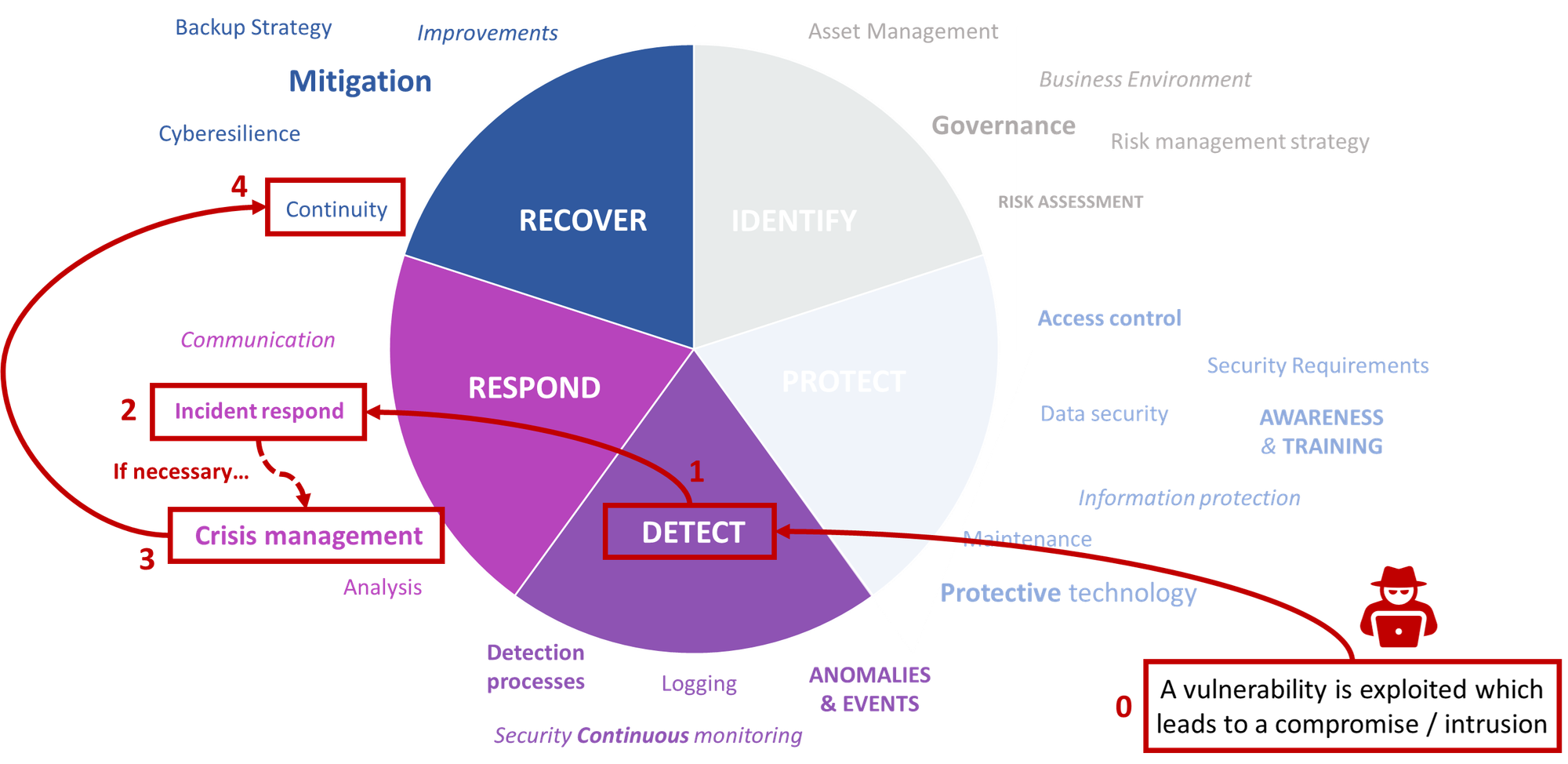
We aim to distinguish 3 different phases of a cybersecurity crisis :
- The incident response is the phase where the events can be qualified and remediated following the normal process. For example, we detect a brute force attack and we follow the procedure to block the IP. This is quite standard and does not need the crisis unit's help.
- The business continuity plan (BCP) starts whenever the business has been affected by an attack or by any other disruptive event (bug affecting clients). In that regard, the BCP can be activated even before the cybersecurity incident becomes a crisis. For example, if the application has crashed because of a DoS the BCP can be activated to restore the service as soon as possible.
- Finally, a crisis can be declared if the conditions are met to re-qualify the incident as a crisis. For example, a ransomware has been detected on a user endpoint (incident) ; if we expect the ransomware to spread and potentially impact critical production activities we may re-qualify this as a crisis.
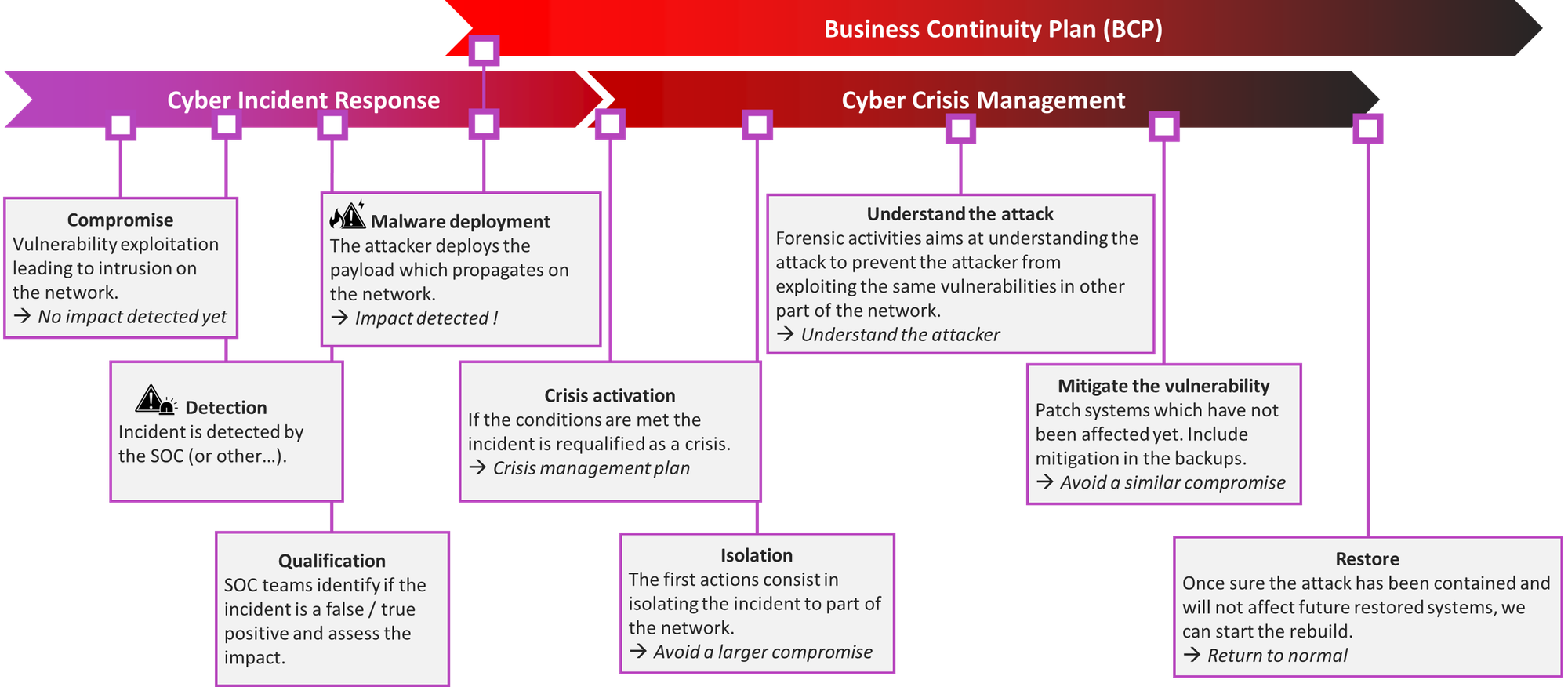
The different stages of crisis management
We have explained that each cybersecurity crisis is unique, as it represents an incident where normal processes no longer function effectively. However, certain activities can be anticipated. These initial actions form part of an overall crisis management strategy that must be adapted to each specific cybersecurity crisis.
A cybersecurity crisis strategy should remain focused on five main activities:
- Isolation: The attack must be contained to prevent additional infrastructures from being affected.
- Understanding: It is essential to analyze the attack path and the attacker’s objectives in order to anticipate their next moves and prevent similar future incidents (the same attack path).
- Mitigation: Once the understanding of the attack has progressed sufficiently, mitigation measures can be implemented to remove the attacker’s presence and traces from the systems (live systems and backups).
- Restoration: After the attack has been contained and mitigated, affected infrastructures can be safely restored without fear of re-infection or further compromise.
- Post-incident review: Return to normal operations and conduct a post-incident review.
The transition from one activity to another is based on criteria defined by the organization and is accompanied by a communication plan directed toward employees, clients, partners, and potentially the media. This communication aims to reassure stakeholders, restore trust, and ensure business continuity. These phases may, however, overlap in practice.
Theoretical action plan
| Action | Objective(s) | Operational Crisis Team |
Deadline / Priority |
|---|---|---|---|
| Open an incident log | Record actions, decisions, and events | Cyber |
Critical At t=0 |
| Contact the cybersecurity crisis management team | Set up the crisis unit | Cyber |
Critical At t=0 |
| Notify the cyber insurance provider | Financial and resource support, contain the attack | Cyber & Legal |
Critical Usually within 48h |
| Notify ENISA and CERT-FR (Cyber Resilience Act) | Legal framework | Legal |
Critical (optional) Within 24h |
| Activate network isolation | Contain the attack | Cyber |
Critical |
| Activate the crisis communication tool | Set up the crisis unit, contain the attack | Cyber |
Critical |
| Inform clients that a cyberattack is in progress | Reputation impact, safety impact | Communication |
Critical |
| Inform employees that a cyberattack is in progress | Reputation impact, contain the attack | Communication & HR |
Critical |
| Provide dedicated workstations to crisis team members | Contain the attack | IT |
Critical |
| Prevent any fund exfiltration from company bank accounts | Financial impact | Sales |
High |
| Inform shareholders that a cyberattack is in progress | Reputation impact, financial support | Communication |
High |
| Restore payroll and dependent HR systems | HR impact | HR |
High |
| Define an HR policy to support 24/7 crisis response activities | HR impact | HR |
Moderate |
| Inform third-party partners that a cyberattack is in progress | Reputation and legal impact | Communication |
Moderate |
| Notify the Data Protection Authority (CNIL) of potential data breach | Legal framework | Legal |
Moderate Within 72h |
| Alert authorities (ANSSI in France, Police, etc.) | Legal framework, limit company liability | Legal |
Moderate Within 72h |
| Secure and isolate regular backups | Contain the attack, support recovery | OT & IT Teams |
Not a priority |
| Preserve traces | Support investigation, evidence collection | OT & IT Teams |
Not a priority |
More details on the rationale and conditions to execute the aforementioned actions in the next blog post.


