What is a bastion and why would you need one ?
A bastion host is a system designed to offer a secure, centralized entry point for accessing administrative tools and environments. It serves as a controlled gateway, enhancing oversight and offering additional features for managing access to critical infrastructure and consoles. In this blog post, I invite you to explore this topic further.
How does a bastion work ?
Here is a digram to better understand how a bastion host works :
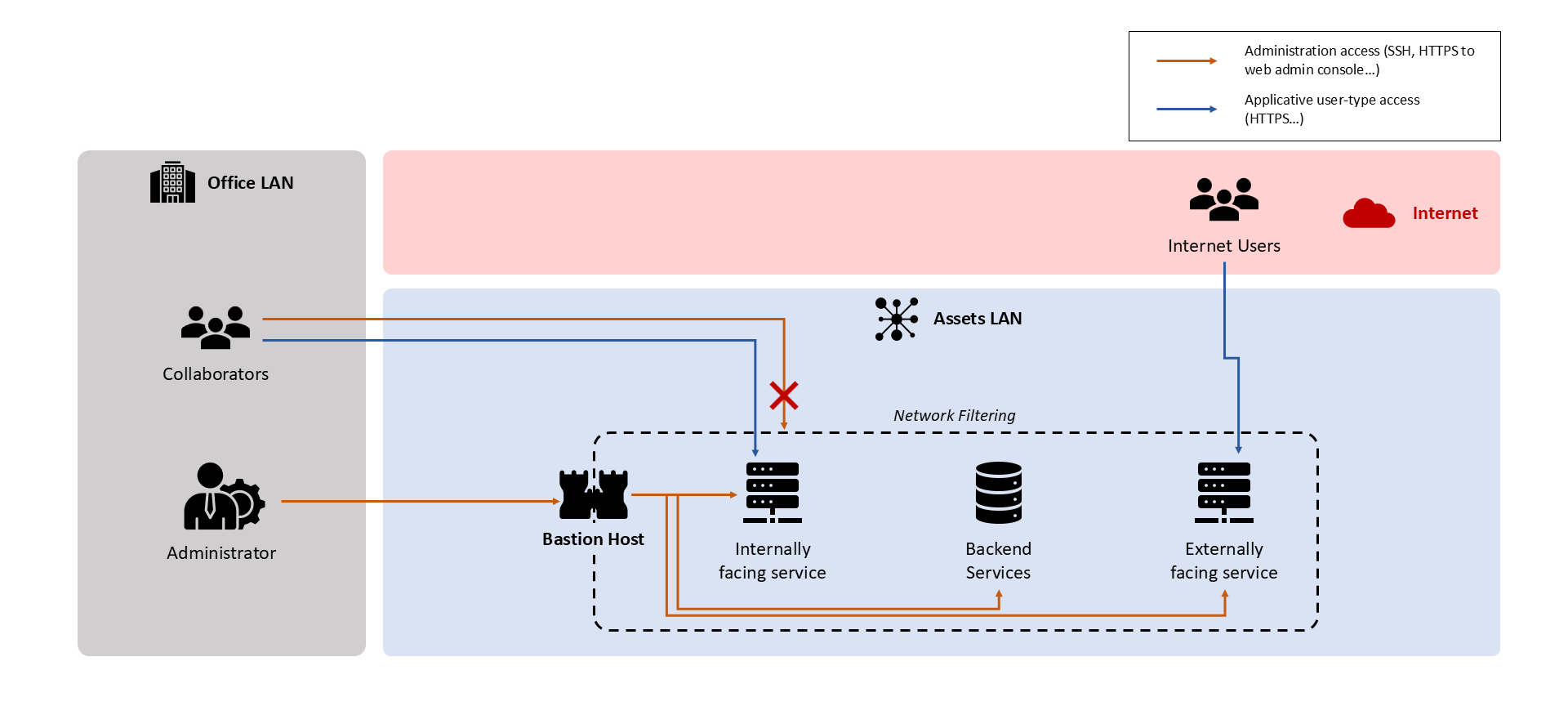
An administrator can only reach an administration endpoint by going through the bastion host.
For example, let's say your administrator uses SSH (TCP 22) to administrate a web server and your collaborators use HTTPS (TCP 443) to access the web service. A bastion host will act as a proxy, an administrator will connect to the bastion using its webGUI and the bastion will relay the connection with SSH. If a collaborator or an administrator tries to reach the web server using SSH directly the firewall will block them because that would mean bypassing the bastion host.
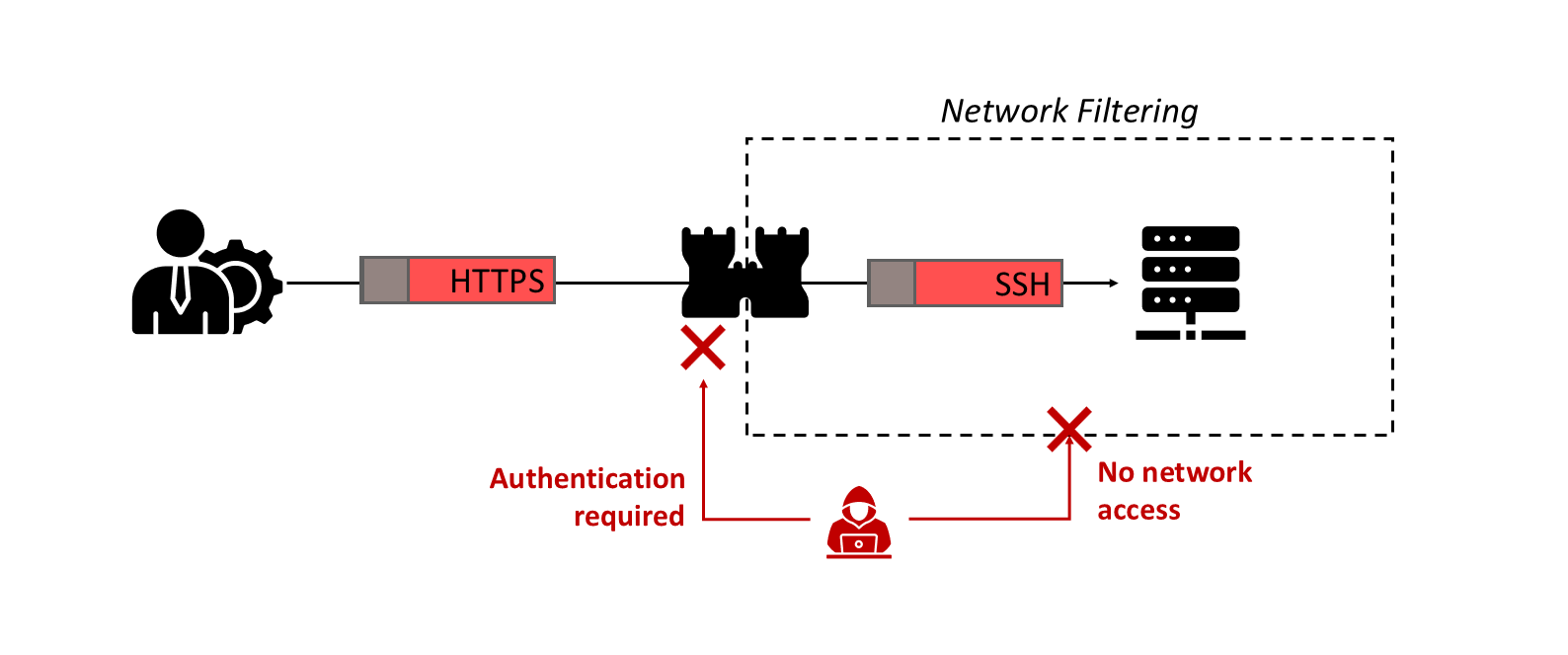
Why would you need a bastion ?
There are a few advantages in using a bastion host to secure the administration of your resources :
- A bastion allows centralized authentication for all administrators. An administrator logs in to the bastion interface and can have admin access to the different resources without remembering the admin password of each server. The bastion acts as a vault managing the admin credentials for the administrators.
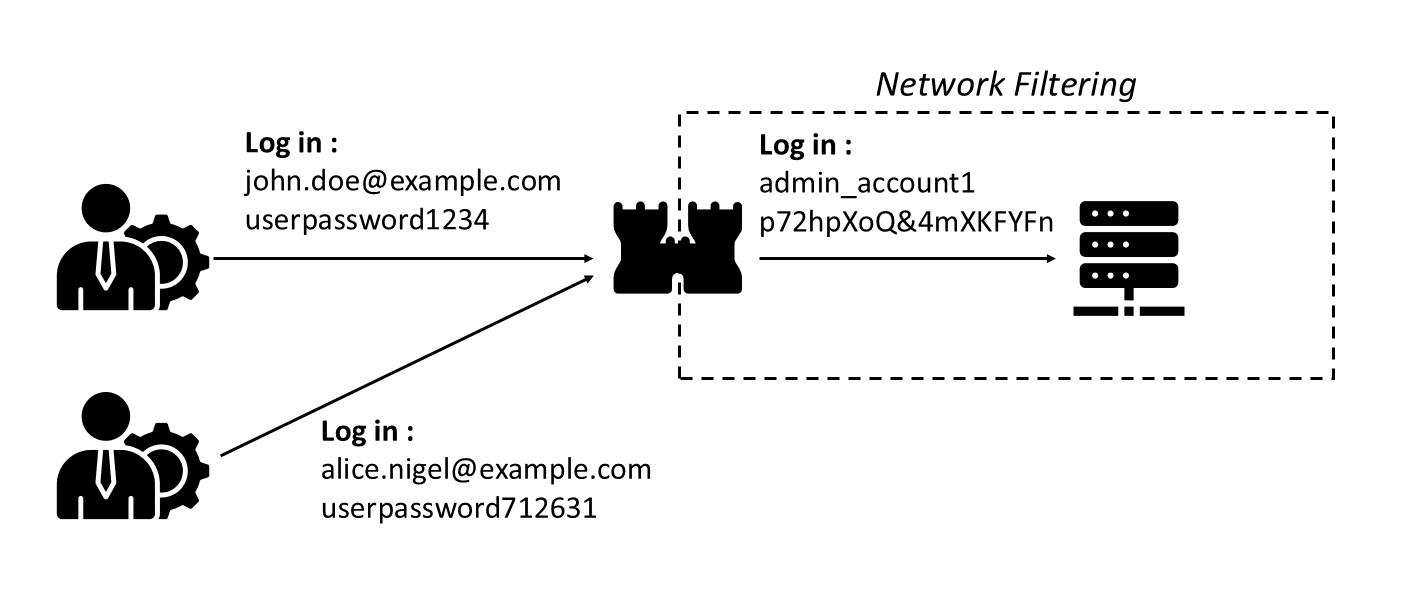
- A bastion can introduce MFA authentication for the administrators even if the ressource to administrator does not support that kind of authentication.
- A bastion can connect to a source of identity like an Active Directory to keep up with HR movement in the company. If our administrator John Doe leaves the company, there is no need to go to each resource he used to administrate and delete his account. Note : integrating the bastion with a centralized identity management system can be risky as it creates dependencies and creates new attack paths.
- A bastion can rotate the admin resource account after each use or after some time. This prevent password sharing, brute force attacks and persistence attemps from being successful.
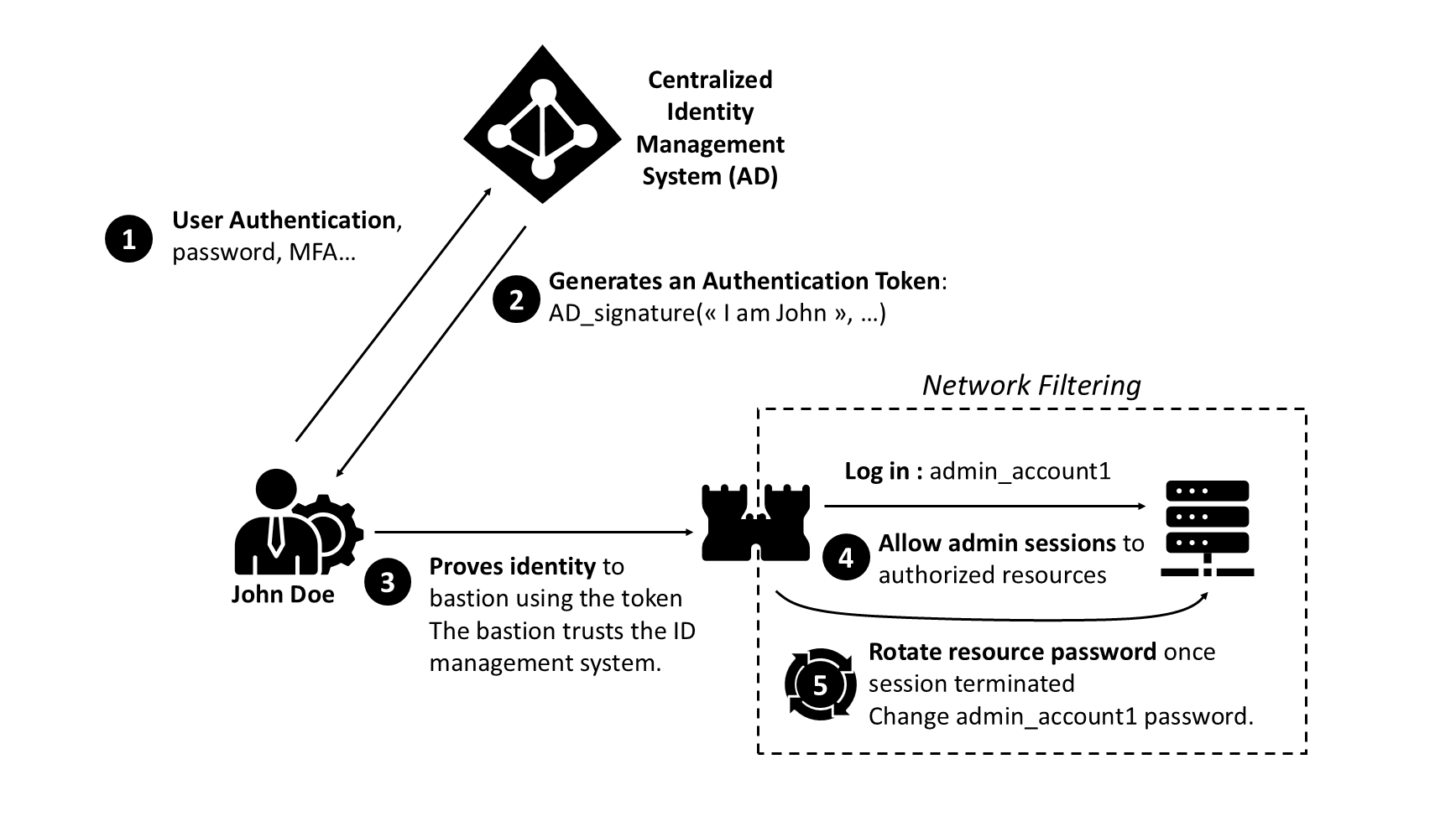
- A bastion improves the traceability of the actions performed by the administrators by recording logs of all the commands going through it. By using a bastion the logging policy can be the same accross all sensitive resources and admin protocol (RDP, SSH...). Leading bastion market players such as CyberArk and Wallix also offer session video recording to enhance traceability. The traceability of admin actions is no longer handled at the resource-level but at the bastion-level.
Doesn't a bastion represent a single point of failure?
If your network filtering is in place and you have no way of easily bypassing the bastion, then yes it is a single point of failure. Still the benefits of having a bastion for security outweights the drawbacks. Installing a bastion is a trade-off between administration integrity and administration availability. In the vast majority of cases, the integrity of your administration is preferable to the availability of your administration access.
To prevent a bastion from being unavailable you can take a few actions :
- Implement a high-availability architecture for the bastion server.
- Create local break-glass admin account in case your centralized ID management system is down. Note : protect these accounts ! See next section.
- Take backup of the bastion vault containing all admin resources credentials.
- Harden the configuration...
How does one administrate a bastion ?
Well, I understand you don't want to setup a bastion to administrate the bastion. Usually you have local admin accounts, separate from the centralized ID management system allowing to administrate the bastion. You will need to protect these accounts, here are a few thoughts :
- Setup MFA for these local admin accounts (duh).
- If the bastion solution allows it, you can have two web consoles to connect to the bastion : one for the centralized ID management system accounts (bastion.example.com) and one for local accounts (bastion.example.com/local_auth). You can setup a proxy not to allow network access to the local authentication console except from some IP or VLAN.
- Create detection rule in your SIEM to detect unwanted local account usage...
That's it, that's all I wanted to say on bastions for now. I hope this blog post was interesting and gave you an overview of their potential benefits.
